DIGITAL SOLUTIONS
Social Engineering: targeting the weakest link
Even with the most sophisticated technical and physical security controls, the success of securing an infrastructure or a network heavily depends on the ability of your employees, contractors and vendors to recognise a cyberattack. For only then can they avoid committing a serious and potentially damaging human mistake. Cybercriminals are well aware of this alarming fact, which is why humans are invariably their first target.
December 6, 2021

When it comes to cybersecurity, people tend to think of it strictly as an engineering issue or an IT challenge. The purely technological lens through which they view this relatively new security practice only registers certain specific aspects of it, such as the use of passwords and updates. Or more common yet: hackers performing feats of technical wizardry with pieces of malware, propagating and exploiting all kinds of computer bugs. While these aspects are all an integral part of today’s cybersecurity landscape, that limited vision is missing a crucial non-technical element: the fact that humans can be tricked into helping their attackers.
Too often we humans are indeed the weakest link in the security chain, as most of us have little or no knowledge to help us identify the many risks and dangers we are facing online. Several attacks and techniques – or attack vectors, in security jargon – exist for cybercriminals to take advantage of this fact. This field of psychological manipulation is called social engineering and one of its most famous techniques is known as phishing.
Why social engineering works
Today, more than ever, cybercriminals rely heavily on social engineering to gain initial access to a corporate network. There are many reasons why this specific attack vector has remained one of the major threats in cybersecurity over the past decade, but here are the most relevant ones:
- Low complexity of attack (in most cases): The information needed to perform a targeted social engineering attack, is usually publicly available, through social media platforms or other public sources.
- No technical expertise required: Successfully executing a social engineering attack requires no advanced skillset or other specific prerequisites on the part of the attacker.
- Limited costs: Common social engineering attacks mainly rely on free email services to deliver a malicious payload to the victim, with sometimes a very basic website to capture the victim’s credentials.
- Targets the most vulnerable asset: Companies implement complex technical controls to safeguard their IT infrastructure and other critical systems. Unfortunately, social engineering attacks exploit the human element, which remains the weakest component of a company’s defense.
How to prevent social engineering attacks
By identifying the techniques used in social engineering attacks, organisations are able to enforce additional controls in order to safeguard their employees against these threats. But again, we see that the techniques used by cybercriminals improve along with the security controls that organisations are implementing. For example, multi-factor authentication (MFA) is inarguably a very strong control to safeguard users and prevent their credentials from being stolen. Unfortunately, cybercriminals have developed sophisticated techniques which allow them to bypass MFA, whether in the form of a push notification or a one-time password (OTP).
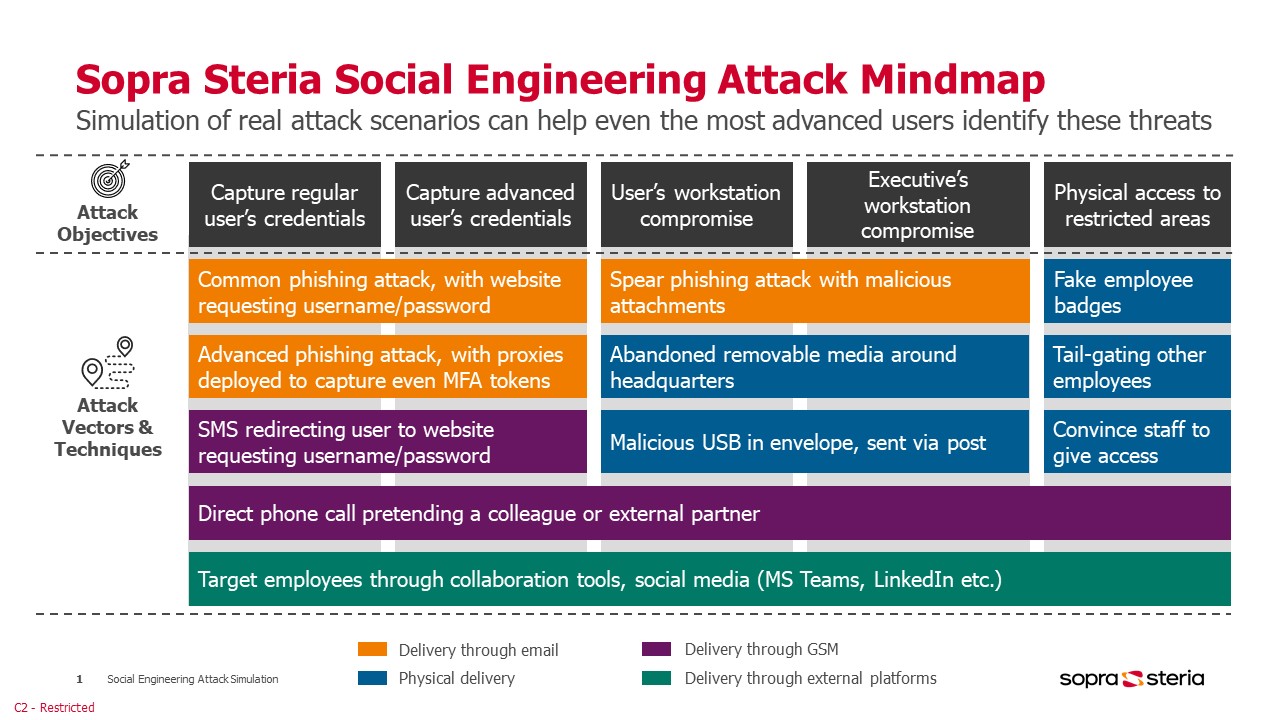
In an attempt to manage the increasing risks of social engineering attacks, companies often choose to simulate basic attack scenarios, to help their employees identify real threats in their day-to-day operations. However, companies need to include more advanced scenarios in their attack simulations as well, so they can also assist their more advanced users in identifying modern, more elaborate attack techniques. Especially since these techniques can have a downright catastrophic impact on their organisation.
User awareness framework
Evaluating your employees’ readiness to identify, prevent and resist social engineering attacks should be a key part of any organisation’s security programme. Therefore, at Sopra Steria, we help our customers maintain a user awareness framework that simulates attack scenarios of scalable complexity.
We can rely on our extensive experience in large-scale cybersecurity projects to create realistic phishing simulations as part of our Social Engineering Services offering. The attack scenarios are designed by taking into consideration the industry in which the customer operates, relevant threat group activities targeting that specific industry, technologies utilised by the customer (VPN, cloud services, collaboration tools, etc.) – or any other publicly available information that can be used to make a scenario more appealing. This approach not only assists companies in simulating real-world attack scenarios, it also helps more advanced users to detect complex attacks in time.
To find out more about our cybersecurity offer, check out our website Or better yet contact Nicolas De Groote or Antonios Marnelis.
- Nicolas De Groote, Cyber Security Consultant – Sopra Steria
- Antonios Marnelis, Cyber Security Consultant – Sopra Steria
